W32.BLASTER
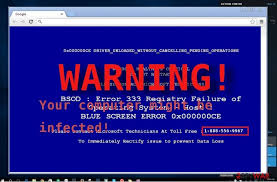
How W32.Blaster Virus Works Spread : The worm spread through an unpatched vulnerability in the Windows Remote Procedure Call (RPC) service (CVE-2003-0352). This allowed it to propagate over the internet and infect machines without requiring any user interaction. Payload : Once the worm infects a system, it could cause the system to crash by sending out repeated requests to ports, ultimately causing a denial-of-service (DoS) attack. Symptoms : Infected systems may experience frequent crashes, slowdowns, or a system shutdown with a message similar to "Your system has been compromised." Full Solution to Remove W32.Blaster Virus Prevention: Patch Your System Apply Windows Updates : Ensure that your system is up-to-date with the latest security patches from Microsoft. The vulnerability exploited by Blaster was fixed in MS03-026 , so it’s essential to install any updates for your version of Windows. Enable Windows Update : Regularly check for updates and enab...