W32.BLASTER
How W32.Blaster Virus Works
-
Spread: The worm spread through an unpatched vulnerability in the Windows Remote Procedure Call (RPC) service (CVE-2003-0352). This allowed it to propagate over the internet and infect machines without requiring any user interaction.
-
Payload: Once the worm infects a system, it could cause the system to crash by sending out repeated requests to ports, ultimately causing a denial-of-service (DoS) attack.
-
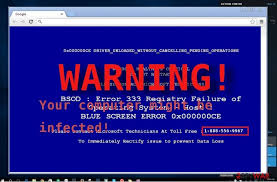
Symptoms: Infected systems may experience frequent crashes, slowdowns, or a system shutdown with a message similar to "Your system has been compromised."
Full Solution to Remove W32.Blaster Virus
-
Prevention: Patch Your System
-
Apply Windows Updates: Ensure that your system is up-to-date with the latest security patches from Microsoft. The vulnerability exploited by Blaster was fixed in MS03-026, so it’s essential to install any updates for your version of Windows.
-
Enable Windows Update: Regularly check for updates and enable automatic updates if it’s not already enabled.
-
-
Disconnect from the Internet
-
To stop the virus from spreading to other systems, disconnect the infected computer from the network (either by unplugging the Ethernet cable or disabling the Wi-Fi connection).
-
-
Run an Antivirus Scan
-
Use a reliable antivirus: Run a full system scan using a reputable antivirus program to detect and remove the W32.Blaster virus. Some antivirus programs that can detect and remove it include:
-
Norton Antivirus
-
McAfee
-
Kaspersky
-
Avast
-
-
Update virus definitions: Before running the scan, update the antivirus definitions to make sure it can recognize the latest threats.
-
-
Manually Remove the Virus (If Necessary) If the antivirus fails to remove the worm, you can manually delete it. Follow these steps:
-
Stop the Worm Process:
-
Open the Task Manager by pressing
Ctrl + Shift + Esc(orCtrl + Alt + Deland selecting Task Manager). -
Look for processes related to the virus, such as
msblast.exe,rpc.exe, or other suspicious entries, and end them.
-
-
Delete the Worm Files:
-
Navigate to the directory where the worm is located (commonly in
C:\Windows\System32\orC:\Windows\Temp\). -
Delete any files named msblast.exe, rpc.exe, or similar worm-related files.
-
-
Remove Registry Entries:
-
Open the Registry Editor by typing
regeditin the Run dialog (pressWindows + Rand typeregedit). -
Navigate to the following registry keys and delete any entries related to the worm:
-
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\ -
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\
-
-
Delete any suspicious entries pointing to the worm files.
-
-
Remove Network Access:
-
Open the Command Prompt (
cmd) and type the following commands:netstat -anoCheck for any suspicious active connections related to the worm and block them via firewall settings.
-
-
Disable Remote Desktop:
-
If you don’t need Remote Desktop, disable it to prevent further exploits.
-
Go to Control Panel > System > Remote and uncheck “Allow users to connect remotely to this computer.”
-
-
-
Run a Second Antivirus Scan After manually removing the files and registry entries, run another antivirus scan to ensure that no traces of the virus remain.
-
Change Passwords
-
After removal, change all system passwords and online account credentials, especially those that could have been compromised by the worm. This step helps protect against potential security breaches.
-
-
Restore from Backup (if necessary) If your system was severely damaged by the worm, consider restoring from a backup made before the infection. Make sure the backup is free of malware.
Preventing Future Infections
-
Keep your software updated: Always install updates for your operating system and software as soon as they are available.
-
Use a Firewall: Enable a firewall (either the built-in Windows firewall or a third-party firewall) to block unauthorized network connections.
-
Use Antivirus Software: Ensure that you have up-to-date antivirus software running at all times.
-
Avoid Clicking Suspicious Links: Be cautious about clicking on email attachments or visiting suspicious websites.
By following this guide, you can effectively deal with the W32.Blaster virus, remove it from your system, and prevent future infections.
My opinion
Comments
Post a Comment